SMS spoofing: What it is and how to protect yourself
When cybercriminals send fake texts impersonating others, they use a shady technique called SMS spoofing. Keep reading to discover how to spot a spoofed text message and how Norton 360 for Mobile can help protect you from SMS scams, malware, and other online threats disguised as innocent texts.

What is SMS spoofing?
SMS spoofing is a technique used to send text messages with a fake sender ID, making it seem like they came from a trusted source, such as a friend, coworker, or bank. Cybercriminals spoof SMS texts to spread malware, link to malicious websites, or trick victims into transferring money or disclosing personal information that leads to identity theft.
According to research by the Federal Trade Commission (FTC), SMS spoofing scams reportedly cost the average victim $1,000 in 2022. Along with other types of phishing, SMS spoofing is becoming more common and harder to detect. And with the rise of AI technology, scam texts are expected to become even more widespread.
SMS spoofing vs smishing
Smishing — or SMS phishing — is the use of deceptive texts in social engineering malware, scam, or identity theft attacks. SMS spoofing is a technique, often used in smishing campaigns, to manipulate sender IDs and mask text messages’ true senders.
How does SMS spoofing work?
To create a spoofed text, some cybercriminals use software to alter the sender ID in the SMS header to display a different name or number. Others leverage hardware such as compromised SIM cards or hacked devices to send deceptive texts.
This means that a spoofed text may even appear in the same conversation thread you've previously used to communicate with the legitimate contact.
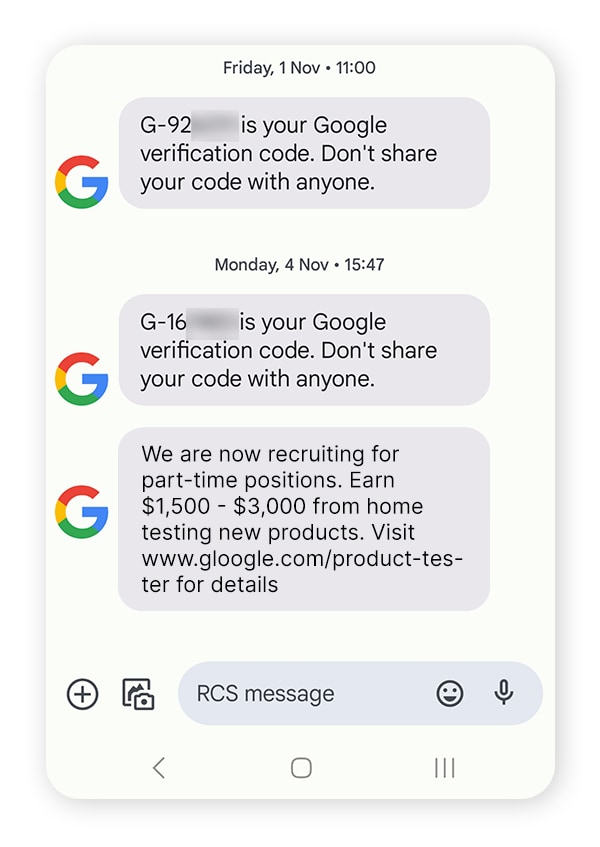

Here are some of the ways attackers send spoof texts:
- SMS spoofing apps: Dedicated apps can alter text sender IDs, making messages appear to come from a different number.
- SIM swapping: Scammers can trick mobile carriers into giving them access to a customer’s SIM card, letting them use the victim’s number to send spoofed messages.
- Phishing malware: Malware can give attackers the power to intercept and manipulate outgoing messages from a victim’s device.
- Outsourcing: Cybercrime-as-a-service tools are illegal software that makes it easy for attackers to commit cybercrimes like SMS spoofing.
Is SMS spoofing illegal?
SMS spoofing is illegal when used to commit fraud, identity theft, or spread malware. In 2019, the U.S. Federal Communications Commission (FCC) banned caller ID spoofing of text messages. But legal forms of SMS spoofing do exist. Businesses may “spoof” their numbers to better communicate with customers. For example, a bank might send a message to its clients from a sender ID like “Bank Alert” rather than the actual phone number.
Institutions also use spoofing to send one-time passwords and appointment reminders. By spoofing their messages, recipients are more likely to open them and less likely to think they’re spam texts.
Because of these legitimate use cases, the actual technology spoofers use is not illegal in most states, making it possible to download spoofing apps, which may even be marketed as tools to use for fun pranks. But SMS spoofing can become illegal when the sender’s intent is malicious.
How to detect spoofing
While it’s very hard to detect SMS spoofing based on the sender ID alone, many spoofed texts share common traits that are red flags that something’s not quite what it seems. Learning to identify these signs can help keep you safe from scammers.
Here’s what to look out for:
- Suspicious requests: It’s uncommon for businesses or individuals to ask for money or information via text. If someone makes a request like this, it’s a strong indication that the text is fake.
- Urgent tone: Scammers often try to use fear or urgency to manipulate you into acting without thinking. You may get a spoofed message from your bank informing you that your account will be locked unless you provide your PIN immediately.
- Unusual phone numbers: If you get a suspicious text from a known contact, cross-check the sender’s number with the contact saved in your phone. If the numbers are different, it’s likely a scam.
- Grammar and spelling mistakes: Hackers may intentionally include mistakes to weed out more cautious targets that may not serve as good marks. Check the spelling of the sender ID. You might notice that a known sender's name is spelled incorrectly.
- Links or attachments: Spoofed texts usually contain malicious links and attachments. These phishing schemes are often attempts at infecting your phone with malware to perpetrate further attacks.
- Unclickable sender fields: You can usually click the sender field in a text message to view details about the sender, including their name and number. If the field is unclickable, it means the sender is trying to hide something.
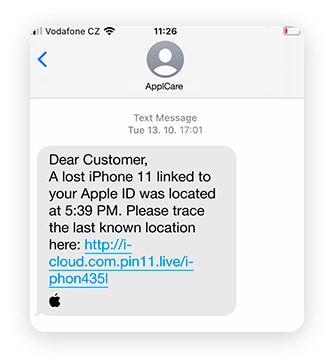

Types of SMS spoofing
Common types of text spoofing include bank impersonation package delivery scams, unsolicited bulk messages, and corporate espionage. Most of these schemes can also be used for caller ID spoofing, where fraudsters call you directly instead of sending a text.
Bank impersonation
Victims of bank impersonation spoofing scams typically receive a text asking them to verify a large transaction, often by responding “yes” or “no.” They are then put through to a fake bank employee who tries to convince the victim to disclose their Social Security number or online banking details.
According to the FTC, bank impersonation was the most frequently reported SMS spoofing scheme in 2022, costing the average victim around $3,000.
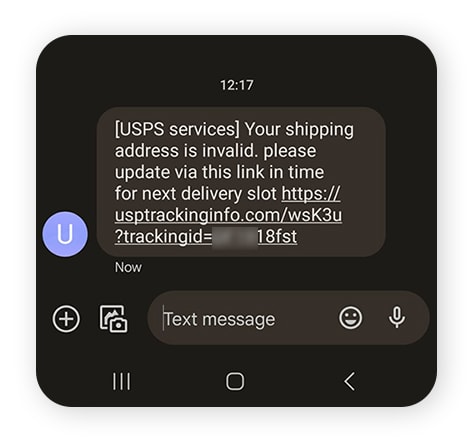
Package delivery scams
In this SMS spoofing scam, victims receive a text claiming to be from a company like UPS, Amazon, or USPS, asking them to confirm delivery details. The link directs them to a fake site that collects personal information, which fraudsters can use to steal identities or make unauthorized credit card charges.

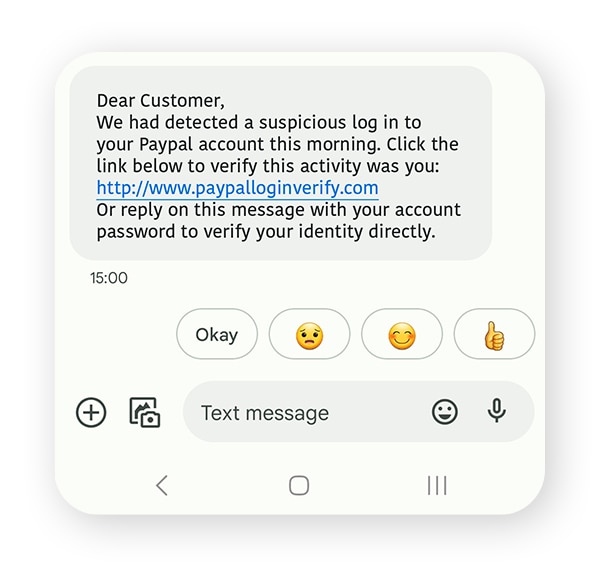
Fake security alerts
Fraudsters send spoofed texts with fake alerts claiming your password was updated, a large Amazon order was placed, or changes were made to an online account. The message includes a malicious link that either installs malware on your device or requests credit card details and personal information.

Unsolicited bulk messages
Scammers often send spoofed messages in bulk to a large number of recipients. These messages are likely to look like spam, but if they are sent to enough people, some are guaranteed to take the bait. Such spoofed texts often claim you’re the lucky recipient of a gift or sweepstakes. They may also advertise a job opening that promises you a lot of money for not a lot of work.
Fake money transfers
Fraudsters use text spoofing to trick you into sending them money. Messages often say they’ve transferred money into your account. The text will request you to complete the transaction or provide personal information by clicking a malicious link.
A scammer may also claim to have accidentally sent money into your account using Venmo or Cash App. The sender will ask you politely to return the money, often to a different account. What you don’t know is that the original “accidental” payment will be reversed by the app, so you’ll lose that money plus the amount you refunded.
Romance scams
A spoofed SMS can also be used to carry out romance scams such as catfishing. Attackers gain their victims’ trust by pulling at their heartstrings. They manipulate their victims over a long period, often asking for regular payments.
Corporate espionage
Spoofed messages can be used to target the phones of corporate employees. This is usually done to steal valuable confidential data. Hackers often attempt to install spyware, a type of malware, onto victims’ phones so they can access corporate emails, passwords, documents, and more.
Even senior-level executives are targeted by hackers in whaling SMS attacks. In fact, executives are much more likely to become victims of spoofing than their employees.
Harassment
Sometimes, attackers use spoofed text messages to harass victims for personal reasons. Spoofing can be used by stalkers, bullies, and anyone holding a grudge. Their goal is often to intimidate or scare a victim into doing what they want.
Can someone send text messages using my number?
Yes, someone can send spoofed text messages using your number. Hackers can gain access to it via a SIM swap scam, by infecting your phone with malware, or by using a spoofing app. They can then send text messages pretending they’re you.
Scammers usually do this when they want to text their targets from a local number. A scammer could also target someone you know and try to trick them.
How do I know if my number is being spoofed?
If your number is being spoofed, you might get text messages or calls from strangers asking who you are. Or, you may receive text message responses to a conversation you haven’t been a part of.
The impact of SMS spoofing
Malicious SMS spoofing has a major impact on individuals, businesses, and the economy. Text message scams and SMS spoofing attacks resulted in a reported $330 million in consumer losses in 2022, according to the FTC. But people lose more than just money as a result of mobile scams. It can cost them their jobs, reputation, and countless hours trying to reverse the damage.
Here are just a few of the consequences of SMS spoofing:
- Financial losses: Most scammers are targeting your money. Whether it’s by asking you for a direct payment, stealing your identity, or accessing your accounts, they will try to get as much as they can.
- Business disruptions: Spoofed messages can cause costly business setbacks, such as website crashes, supply chain disruptions, and security breaches.
- Reputational damage: Businesses and individuals may be blamed for the actions of the hacker who spoofed them. Customers may conclude that the business isn’t serious about cybersecurity and data protection.
- Legal liabilities: Victims of SMS spoofing may face legal issues, especially if their personal info or devices are used to harm others or make unauthorized transactions.
What is the government doing to combat spoofing?
Government agencies and law enforcement are actively targeting SMS spoofing and related attacks like IP, email, and website spoofing. Federal laws ban fraudulent practices, including fake texts, and establish clear enforcement guidelines. And agencies like the Federal Communications Commission (FCC) enforce strict rules on spoofing, requiring mobile carriers to implement protections such as STIR/SHAKEN and the Robocall Response Team.
Despite the work of regulators and law enforcement, SMS spoofing and other phishing attacks are not going away. As technology advances, hackers will always find a way to slip their attacks past the safeguards. That’s why it’s up to you to educate yourself on spoofing to help avoid becoming a victim.
Tips on how to stop SMS spoofing
The average person receives dozens of spam texts per month, and any one of those could be a spoofing attack. But just because you receive fake texts doesn’t mean you have to become a victim. It can be tricky to defend yourself from cybercrime — but not impossible.
Following these tips can help protect you from spoof text messages:
- Block unknown numbers: If you receive spam or random texts from unknown numbers, block them. This will prevent those numbers from spamming you in the future.
- Avoid clicking SMS links: Be very careful clicking links sent via text, even if you think you know the sender. If you really want to click a link, contact them via a different messaging service to confirm they sent it.
- Beware of password reset texts: Don’t respond to an unsolicited SMS request to reset your password. Banks and other organizations won’t ask you to do this via text.
- Don’t share personal information: Most organizations will not ask you to share personal information or passwords over SMS. Remember that small details about you can add up quickly and could be the final piece a fraudster needs.
- Enable spam filters: Turn on your phone’s spam filters or install a spam-blocking app to stop spam texts.
- Don’t respond instantly: If you get a text urging you to do something immediately, consider it a red flag. Confirm that it’s a legitimate SMS before taking action by calling the official number listed on their website.
- Update your software: Always keep your phone’s operating system and apps updated to help patch vulnerabilities and mitigate risk.
- Install cybersecurity software: Robust antivirus software like Norton 360 for Mobile helps shield your phone from threats and protect you if you accidentally click a malicious link.
Use comprehensive cybersecurity to stay safer online
Following the tips above can help you avoid falling victim to an SMS spoofing scam. But staying vigilant and constantly monitoring your messages can be difficult, especially when you’re pressed for time. That’s where reliable online security software comes in.
Norton 360 for Mobile is a powerful suite of security tools designed to protect against malicious links, dangerous websites, and other digital threats that can be hidden inside spoofed texts. Install Norton 360 for Mobile to help protect your phone, your identity, and your digital life.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips and updates.