Watering hole attack: definition + prevention tips
Watering hole attacks are coordinated, large-scale attacks on the website of an organization or business. By infecting a website visited by specific targets, cybercriminals turn that site into a so-called watering hole that can then pass the infection on to any website visitors. Keep reading to learn more about watering hole attacks. Then, get Norton 360 Deluxe to help block hacking attempts and keep your personal information safer.

What is a watering hole attack?
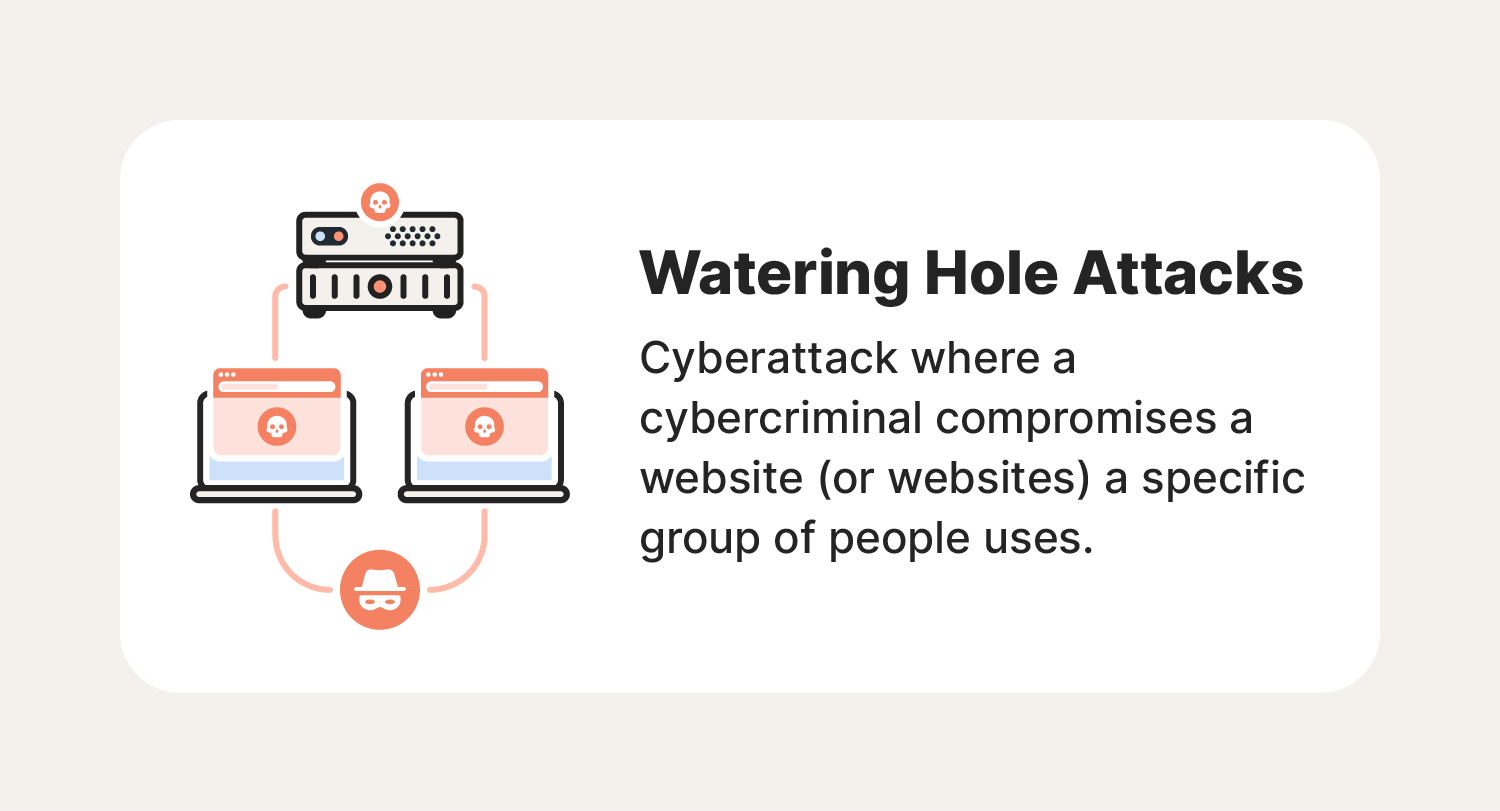
A watering hole attack is a type of cyberattack in which a cybercriminal infects a website frequently visited by a target with the goal of infecting the target’s computer. Rather than attacking a target directly, a watering hole attack targets a website often used by a specific group of people. Through a watering hole attack, cybercriminals aim to infect user devices with malware or gain access to organizational databases and personal data.
These attacks get their names from natural watering holes, where groups of animals congregate and are at ease. That gives predators the chance to strike where the prey least expects it. The large number of victims in one place helps improve the predator’s chances of success. Common targets of watering hole cyberattacks include large companies, governments, financial institutions, and other groups with a high level of security.
By attacking a network of connected computers, a cybercriminal will increase their chances of success compared to hacking targets individually. While the image of an apex predator quickly striking an animal is powerful, it’s important to note that these attacks are usually designed as an advanced persistent threat (APT). In an APT attack, a hacker establishes a long-term connection to their target to steal as much information as possible without being detected.
How watering hole attacks work
Watering hole attacks aren’t spontaneous attacks of opportunity. Hackers and cybercriminals carefully track their prey before springing their trap. Understanding the process can help you recognize and avoid potential threats circling the websites you frequent.
1. Criminals observe their target(s)
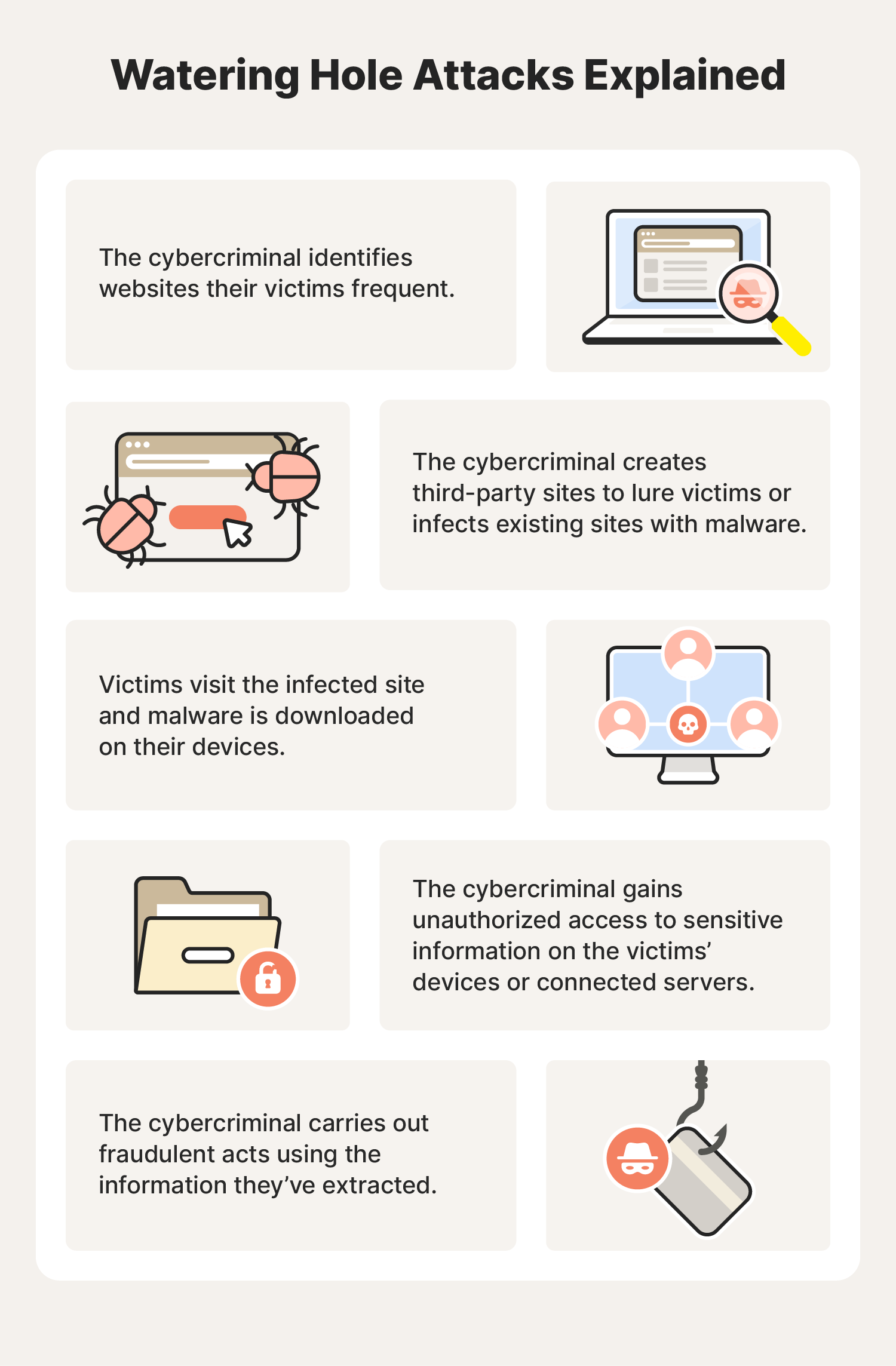
Instead of taking a run directly at a target, cybercriminals will watch their targets in several different ways. They will probe the system’s attack surface, looking for vulnerabilities and any honeypots the site’s security team placed. The cybercriminals will also examine all of the pages and subdomains on a site for any lax security.
They’ll also take a broader view by searching for more information about the people working for or with their target. The criminal might use a public-facing website, such as social networking sites, to learn the names of employees or find employees, vendors, and other contacts connected to an organization.
2. Criminals analyze what they’ve learned
Once the attacker has some data to work with, they’ll sniff out ways to exploit system vulnerabilities and human beings.
The scammer might even create malicious websites and fake emails to phish more information about a system from the people using it. While many of these watering hole phishing schemes focus on the broadest section of a user base, cybercriminals may also attempt to spear phish specific people.
3. Criminals plan their attack
During the planning phase, the cyberattacker will create the tools and resources needed to launch the attack. This includes everything from modifying existing malware to accomplish a specific task to rewriting third-party software to create backdoors into every machine where it’s installed.
Finally, the cybercriminal will set up the malicious software and prepare to run it on the site or service they chose to target.
4. Criminals launch their attack
The attack will occur when the cybercriminal deploys the hack or malware onto the compromised site or service. Depending on the malware’s design, it may take some time before the infection of connected devices, networks, and software is complete.
As the malware spreads, it sends information back to the cybercriminal. Hackers can use watering hole attacks for the following aims:
- To collect data to sell on the dark web.
- To threaten an organization with compromised data.
- To sell data to a competitor.
- To use data or info as a ransom.
Watering hole attack prevention tips
Now that you understand what these attacks are and how criminals plan them, it’s important to know how to avoid one. Follow these tips for watering hole attack prevention to keep you and your information safe and secure.
Educate yourself
If you want to do your part to prevent a watering hole attack, learning what they are and how cybercriminals can gather information about your habits is the first step.
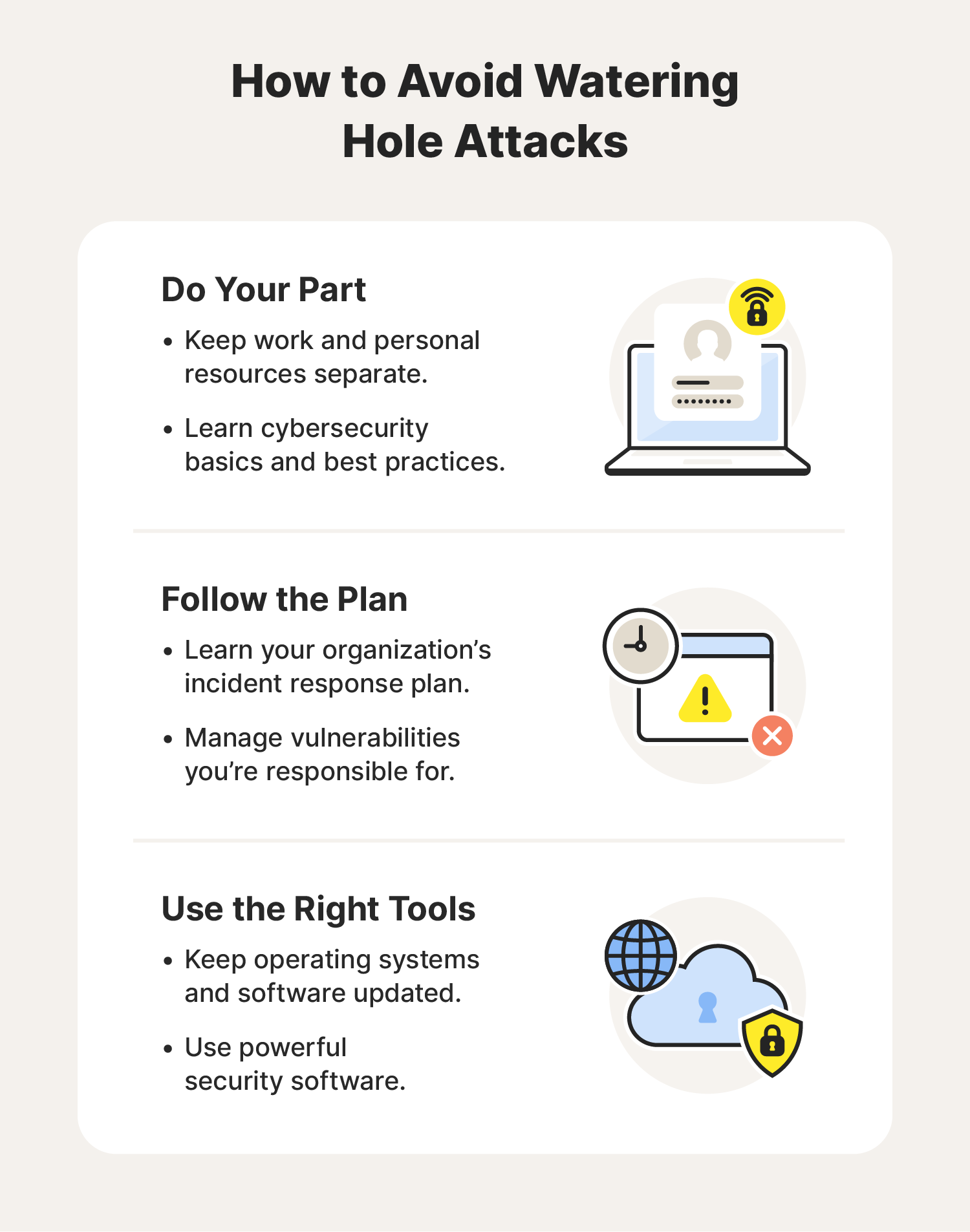
- Keep work and personal resources separate: Working from home can create vulnerabilities in your organization’s network and systems. Only use devices your company approves, and don’t sign into personal networks and accounts on work devices.
- Learn cybersecurity basics: Cybersecurity starts with individual users. Practicing good password security and avoiding pop-ups and messages from unknown senders can help create a safer online environment. VPNs and firewalls are other tools that help keep online connections more secure.
Create and follow a plan
Staying on top of some of the best cybersecurity practices and knowing when to use them will help your organization recognize and stop a watering hole attack.
- Know your incident response plan: For an organization to deal with a watering hole attack, it needs a plan. Ensure you understand what your organization expects from you if the time comes.
- Take part in vulnerability management: No plan or system will ever be completely secure from threats. Actively searching for ways to reduce vulnerabilities in your daily work can greatly help your cybersecurity team.
- Isolate sensitive systems: Response plans should feature directions for securing the most sensitive systems, usually financial data, customer information, and proprietary secrets.
- Monitor network traffic: A basic understanding of network traffic can help you detect and alert your organization’s cybersecurity team. Monitor your traffic whenever you access restricted data and know how to disconnect from the network in the event of an attack.
Use the right tools
Whether you’re in charge of cybersecurity for your organization or you’re working far from the office, the right tools are helpful when you’re trying to stop a watering hole attack before it happens. These tools can help you prevent watering hole attacks:
- Web filters: Filtering out certain sites means you’ll be less exposed to watering hole attacks (and other cyberattacks). Depending on the nature of your organization, filtering might mean blocking third-party apps when using organization resources and devices, or it might look like a more limited experience on the web.
- Software updates: Software updates and patches enhance performance and patch security flaws in an operating system, firmware, or software. Turn on automatic updates or follow your group’s standards for updates.
- Security software: When you use security software, you get protection that goes beyond what you could do on your own. Reliable antivirus software can help stop malware in its tracks, prevent pop-ups that cybercriminals may load with spyware or viruses, and even reduce your risk of falling for a phishing attack.
Get Norton 360 Deluxe to help block hacking attempts, reduce the chances of fake sites stealing your information, and keep your devices running smoothly.
Watering hole attack examples timeline
The scope of watering hole attacks means that they’re rare but also very large. Here is a timeline of real-world watering hole attacks over the years.
- 2012: The U.S. Council of Foreign Relations was infected by malware via a weakness in Microsoft’s Internet Explorer, impacting thousands of users nationwide.
- 2013: Attackers accessed the U.S. Department of Labor to gather information on thousands of users who researched or visited nuclear-related content.
- 2015: The Forbes website was attacked by a cyberespionage group operating out of China.
- 2017: A country-wide watering hole attack in China via Microsoft lasted from late 2017 to March 2018.
- 2019: Hackers hid malware as an Adobe Flash update that targeted Asian religious and charitable organizations.
- 2021: The “Live Coronavirus Data Map” from the Johns Hopkins Center for Systems Science and Engineering spread malware among users nationwide.
Watering hole vs. other related cyberattacks
Because of the complex nature of watering hole attacks, hackers and cybercriminals often have to use various hacking techniques to successfully launch a watering hole attack. Cybersecurity experts also use these techniques to find, track, and prevent hackers from accessing secure data.
By understanding the common components of these attacks, you can help prevent them from happening (or, at the very least, reduce their impact). Here are some techniques hackers might use to help set up a watering hole attack:
- Man-in-the-middle attacks happen when hackers set up a legitimate website or service and, from there, lure users to share their sensitive information. Cybercriminals can use this information to inform how they plan and carry out a watering hole cyberattack.
- Honeypots are a computer or computer system intended to mimic likely targets of cyberattacks. They detect attacks or deflect them from a legitimate target. Cybersecurity teams can also use them to track and observe hackers.
- Supply chain cyberattacks are when hackers infiltrate a trusted software or IT company to inject malware into software updates. Then, when the service company installs those updates on its customers’ computers, those devices are automatically infected.
- Tailgating is when a cybercriminal tricks employees of a certain company into helping them gain unauthorized access to the company database. A hacker does this physically by following an employee into a building or impersonating someone with access.
- Social engineering is when a cybercriminal manipulates someone into exposing sensitive or confidential information, often through digital communications. The cybercriminal may create a fake email address that looks like the employee’s manager or another employee to gain access to sensitive information.
Protect your data and your identity
Learning the signs of a hacking attack and using security software can lower your risk of becoming a victim or having your data compromised. Norton 360 Deluxe can help block malware, protect the data you send and receive online, and prevent you from navigating to sites that could steal your passwords.
FAQs about watering hole attacks
Still curious about these cyberattacks? We have answers.
What are some common targets for watering hole attacks?
The most common targets for watering hole attacks include highly competitive industries and other entities with normally high security, like governments and financial institutions. Instead of directly attacking those targets, cybercriminals will search for a backdoor through connected partners or vendors.
What is the difference between spear phishing and watering hole attacks?
Spear phishing is a targeted attack on a small group of people (or an individual), whereas a watering hole attack targets anyone (and everyone) using a specific website. Water hole attacks are attacks of opportunity where the hacker will steal whatever data they can get in the hopes that it allows them to access something valuable. Spear phishing, by contrast, focuses on a small group to extract specific information or system data.
How common are watering hole attacks?
Watering hole attacks aren’t too common due to their time-consuming and labor-intensive nature. Most hackers prefer easier targets because of the amount of work it takes to prepare one of these attacks (and because they usually target large-scale organizations).
However, if there is a watering hole attack, many people outside these organizations are affected, especially if a data leak contains personal information, like medical records or financial accounts.
What will an attacker develop to trick users during a watering hole attack?
Some attackers will create fake websites and emails for phishing purposes. They may also use malvertising or scareware to trick users into downloading fake security software that contains spyware or other malicious software.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips and updates.